The Emerging Way Around 2FA
With individuals and companies understanding that security and phishing risks are rising, the implementation of 2FA (2 Factor Authentication) has become increasingly more prevalent. 2FA allows users to add a level of security by adding another “factor” besides their usernames and passwords that they must enter correctly to gain access to their account. Typically, 2FA is enabled as a security feature on more high-risk accounts such as finance applications or email, but as the threat increases, it’s becoming utilized on more sites and apps.
As technology progresses, the social engineering capability does as well. Instead of a standard phishing attack where you receive an email or text message on a phone number with a dummy link, click the dummy link, then enter your (very real) banking information. The hacker then takes that information, tries it on the real banking site, and gains access to your bank account. You can read more about how phishing works here.
As 2 Factor Authentication becomes more prominent, the depth of these phishing-style attacks also increases. Attacks are now being sent through text messages making it more difficult to sense their legitimacy. See a Chase website scam example below:
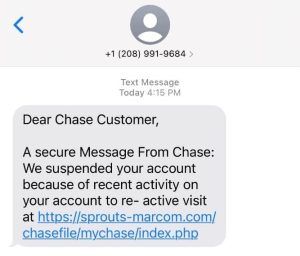
The way these attacks are conducted is as follows:
Step 1: You’ll receive a text message like the one above from a “trusted” institution like Chase or Bank of America, explaining some reason why you need to access your online banking account or credit card.
Step 2: You click the link leading you to a dummy online banking page that looks identical to a Chase or Bank of America Website.
Step 3: The website asks you to “reset” your password asking you to enter your old username and passwords and then your new one.
Step 4: Within 15-30 seconds, that information is plugged into the actual Chase of BOA website, but you have 2FA enabled.
Step 5: You get a real text from the financial institution asking you to input a code on their site (the one the hackers are currently logging into); however, the dummy site also asks for the code.
Step 6: You input the 2 Factor Authentication code into the dummy site, and hackers now have your passwords and 2FA code and have gained full access to your account.
Once a hacker gains access via 2FA, it’s pretty much over for any information behind that wall, they can use the same technology that got them in there to keep you out. Typically, by the time you’re able to allow the company to grant you access to the page, they’ve already done what they needed to do.
The Most Common 2FA Bypass Attacks
Two-factor authentication (2FA) stands as a crucial defense against unauthorized access, but it’s not impervious to attacks. Let’s delve into some of the most common methods used to bypass 2FA security:
1. Phishing Attacks: Despite 2FA, phishing remains a prevalent threat. Attackers trick users into providing both their credentials and the 2FA code, granting them access.
2. Man-in-the-Middle (MITM) Attacks: In an MITM attack, the attacker intercepts communication between the user and the authentication system, capturing the 2FA code in transit.
3. SIM Swapping: Attackers convince the victim’s mobile carrier to transfer their phone number to a new SIM card under the attacker’s control. This enables them to intercept the 2FA code sent via SMS.
4. Credential Stuffing: Attackers use previously breached username-password pairs to gain access to accounts. If users have reused passwords across multiple accounts, even 2FA may not stop unauthorized access.
5. Social Engineering: Attackers manipulate individuals into revealing sensitive information, including 2FA codes, through deception or coercion.
Understanding these common 2FA bypass techniques is crucial for implementing effective security measures and mitigating the risks associated with them. Vigilance, education, and the adoption of additional security layers beyond 2FA are essential to bolstering the overall security posture.
How to spot a potential 2FA phishing attempt?
There are key factors when it comes to spotting a fraudulent message, much like emails or text messages. If a text contains the following: Misspellings, links that don’t seem consistent with the brand that’s reaching out, broken English, and sometimes improper wording.
These are effective because you could easily miss the aforementioned criteria if you’re not paying close attention. A text message differs from an email because no name, signature, font options, colors, etc., can tell you different things about an email. With text messaging, you have a single font and color, so all they have to do is get the wording and verbiage correct.
These attacks are so widespread that throughout the summer of 2021, the number of phishing URLs designed to impersonate Chase’s website jumped by 300%, says security firm Cyren. That speaks to not only the shift in types of phishing but the effectiveness overall.
What to do to avoid falling victim?
Overall, these campaigns are meant to deceive; attackers know how to trick us. Attackers consider dozens of factors to make us believe the message we have received is legitimate. Here are a few ways you can help yourself not become a victim:
Links – Never click links or dial phone numbers in emails or text messages. When possible, go to a company’s website or mobile app to ensure you’re accessing the right information and not getting targeted for a phishing attack.
Second Opinion – A second opinion thwarts more attacks than you’d expect. The second set of eyes on a questionable message or email is a proven way to make sure that someone else can see the same potential inaccuracies that you are. Often times others have been approached with similar phishing style messages so it’s good to show a friend or family member if you receive something you think is suspicious.
Slow Down – This is a large part of the attacker’s advantage, we’re all so engaged in our lives that sometimes move too fast and don’t ask simple questions like “why is this website link different?” or “why doesn’t this email address have the proper suffix?”. Attackers prey on our ability to trust bigger, very reputable corporations and follow instructions given to us because of their proven trustworthiness. In the end, just slow down and look into anything you receive that regards a high priority account before inputting username and passwords.
Overall, we have to be vigilant and use several security feature when it comes to unfamiliar texts or emails we receive. It’s especially important to help older friends and family members who may not be technologically savvy because they make up a large part of the victims of scams like this one among many others. If something doesn’t look or feel right about a text or email, odds are, it probably isn’t.
Take the help of a partner to enable 2FA and enhance cybersecurity.