CYBERSECURITY FOR BUSINESSES
Protect Your Business From Cyber Attacks
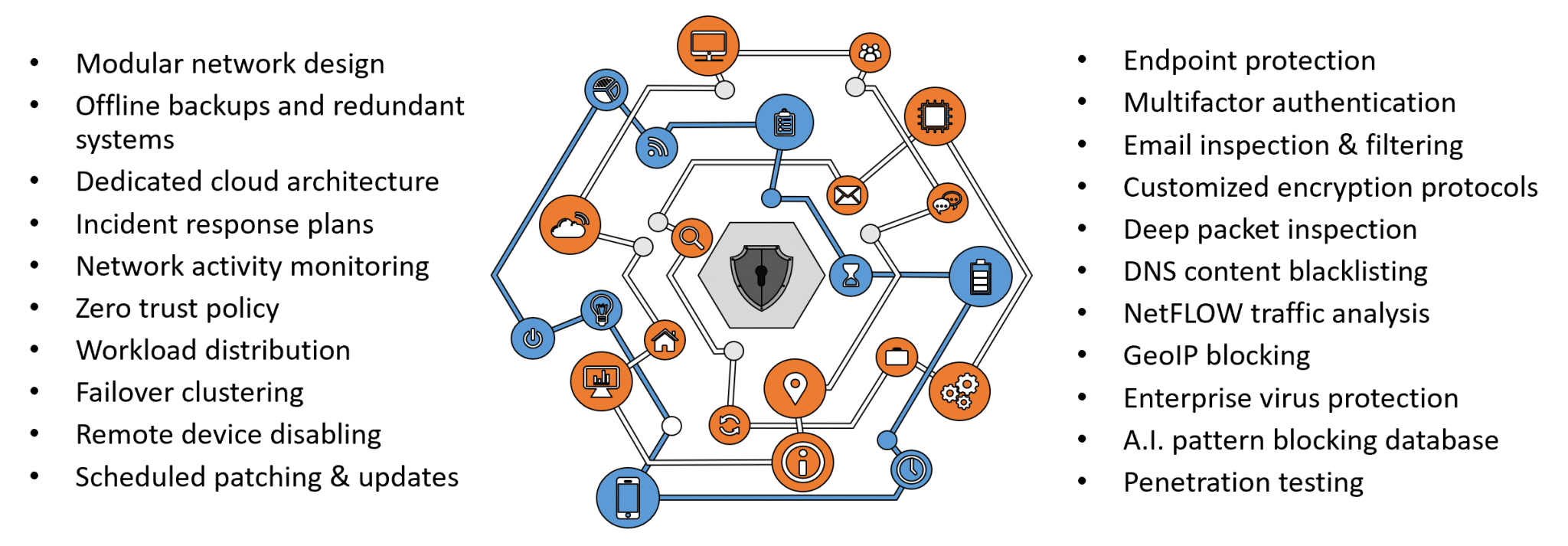
Our team has experience in firewall, threat detection, network security, regulatory, incident response, and cloud-based threats, which are always needed to keep your IT infrastructure safe and secure. Get the best business cybersecurity solutions with data protection and malware countermeasures for your network, email system, and documents.
You did not get into your career to become a cybersecurity or data privacy expert. Let us double-check your setup and make sure the technology that keeps your organization healthy, will also keep it secure.
It’s Time to Prioritize Your Cybersecurity Strategies
That Have the Receipts to Prove It
Malicious Connection Attempts Blocked Each Day
Malicious Connection Attempts Blocked Each Day
Network Flow Records Inspected Per Day
Network Flow Records Inspected Per Day
Downloaded Malware Caught & Eliminated with Zero Incidents Last Year
Downloaded Malware Caught & Eliminated with Zero Incidents Last Year
Workflow Events Logged Everyday
Workflow Events Logged Everyday
Cybersecurity Strategies Built From the Ground up
As part of our ransomware protection for businesses, Zero Trust Security model, we eliminate unnecessary connections, monitor systems, and grant access only to employees who require it. All access is logged and audited on a regular for irregular activities. All devices have antivirus and antispyware software installed. 2FA is implemented to strengthen information security for all Protected Harbor Clients. And a best-in-breed firewall is installed to block unauthorized access, while remote access should be secured using a virtualized desktop.

Our Protected Multi-Layer Approach to Cybersecurity Stops Reputational Damage
We prioritize layered cybersecurity protection, beginning with a sturdy network perimeter composed of a firewall, network management, and regular network inspections. We then include proactive monitoring of your systems, including anti-virus and anti-malware software, DNS filtering, and anti-spam protection. Most importantly, affordable cybersecurity for small businesses, we recommend investing in cyber training for your staff – your employees are the first and finest line of cyber defense.
Cybersecurity Protection Services for New York, New Jersey, & Connecticut Businesses
One IT Company To Keep Your Business, Data, and Customers Secure.
Contact Us
Understand your security threat exposure with a free cybersecurity risk assessment. Great actionable steps you can take to gain a strategic upper hand. We offer risk assessment services specifically designed for companies operating under HIPAA, PCI DSS, Sarbanes Oxley, or DFARs regulations.
When You Join The Protected, You Get An Army
Protected Harbor’s Security Operations Center enables scalable and adaptable threat intelligence and predictive security intelligence for your organization. Our team is staffed with certified security techs and threat hunters from around the globe, providing cybersecurity outsourcing for small businesses, operating 24/7/365 as an optional part of your cybersecurity defenses. We are continuously monitoring, detecting, and remediating threats to keep your data protected as part of our elite service plans. When you join The Protected, you..
- Seal network gaps to stop hackers from breaking into your business.
- Maintain high productivity levels by shielding PCs from viruses.
- Avoid costly regulatory fines by complying with data security laws.
- Prevent embarrassing & costly lawsuits by keeping client data safe.
Leverage A.I. To Stop Threats Before You Know They’re There
Protected Harbor is continuously collecting flow data to aggregate information security, analyze, and visualize network details for viewing in real-time or for historical archiving. Our dashboard gives our proactive monitoring team a view of possible threats contacting or attempting to contact the network, including public threats based on IP reputation, high-risk internal clients based on flow count, visual hot spots of inbound connections, top block ports, and recently blocked traffic.
Who’s doing the most traffic? Are we being flooded? What types of traffic are using the most bandwidth? These questions and more are answered by filtering for results on the Top Talkers Dashboard. We can drill down even further on flow details to find specific traffic streams to analyse from an individual protocol or address.
Cybersecurity for Businesses – FAQs
Cybersecurity is critical because a single breach can lead to devastating financial losses, reputational damage, and legal repercussions. It protects sensitive data (yours and your customers’), ensures business continuity by preventing disruptive downtime, and builds trust with your clients. In today’s digital landscape, a strong security posture is not optional; it’s a fundamental aspect of responsible business operations and risk management.
The most prevalent threats include phishing attacks (deceptive emails tricking employees), ransomware (malicious software that encrypts data for a fee), malware, and insecure cloud configurations. Social engineering preys on human error, while weak passwords and unpatched software create easy entry points for hackers. Businesses must also be wary of insider threats, whether malicious or accidental.
Start with foundational steps: educate employees on identifying phishing attempts, enforce strong password policies and multi-factor authentication (MFA), and ensure all software is consistently updated. Regularly back up critical data and implement a managed firewall and antivirus solution. For comprehensive protection, partnering with a managed security services provider (MSSP) offers expert guidance without the cost of an in-house team.
A business cybersecurity strategy is a proactive, comprehensive plan that outlines how an organization protects its digital assets, data, and systems from cyber threats. It involves risk assessment, defining security policies, implementing layered defenses (like firewalls and access controls), employee training, and establishing an incident response plan. This strategy aligns security measures with specific business goals to manage risk effectively.
Cost varies significantly based on business size, industry, and required security level. Expenses can range from minimal (for basic tools and training) to substantial annual investments for advanced managed services, dedicated staff, and enterprise-grade software. Many view it as insurance; the cost of prevention is far lower than the potential financial impact of a successful cyber attack, which can reach hundreds of thousands of dollars.
Highly targeted industries include healthcare (for valuable patient data), financial services (for direct access to funds), legal firms (for sensitive client information), government agencies, and critical infrastructure (energy, utilities). However, no industry is immune. Small businesses are often targeted precisely because they are perceived as having weaker defenses, making robust cybersecurity essential for all.


