CYBERSECURITY FOR BUSINESSES
Our team has experience in firewall, threat detection, regulatory, incident response, and cloud-based threats, which are always needed to keep your IT infrastructure safe and secure. Get complete data protection and malware countermeasures for your network, email system, and documents.
You did not get into your career to become a cybersecurity or data privacy expert. Let us double-check your setup and make sure the technology that keeps your organization healthy, will also keep it secure.
Malicious Connection Attempts Blocked Each Day
Malicious Connection Attempts Blocked Each Day
Network Flow Records Inspected Per Day
Network Flow Records Inspected Per Day
Downloaded Malware Caught & Eliminated with Zero Incidents Last Year
Downloaded Malware Caught & Eliminated with Zero Incidents Last Year
Workflow Events Logged Everyday
Workflow Events Logged Everyday
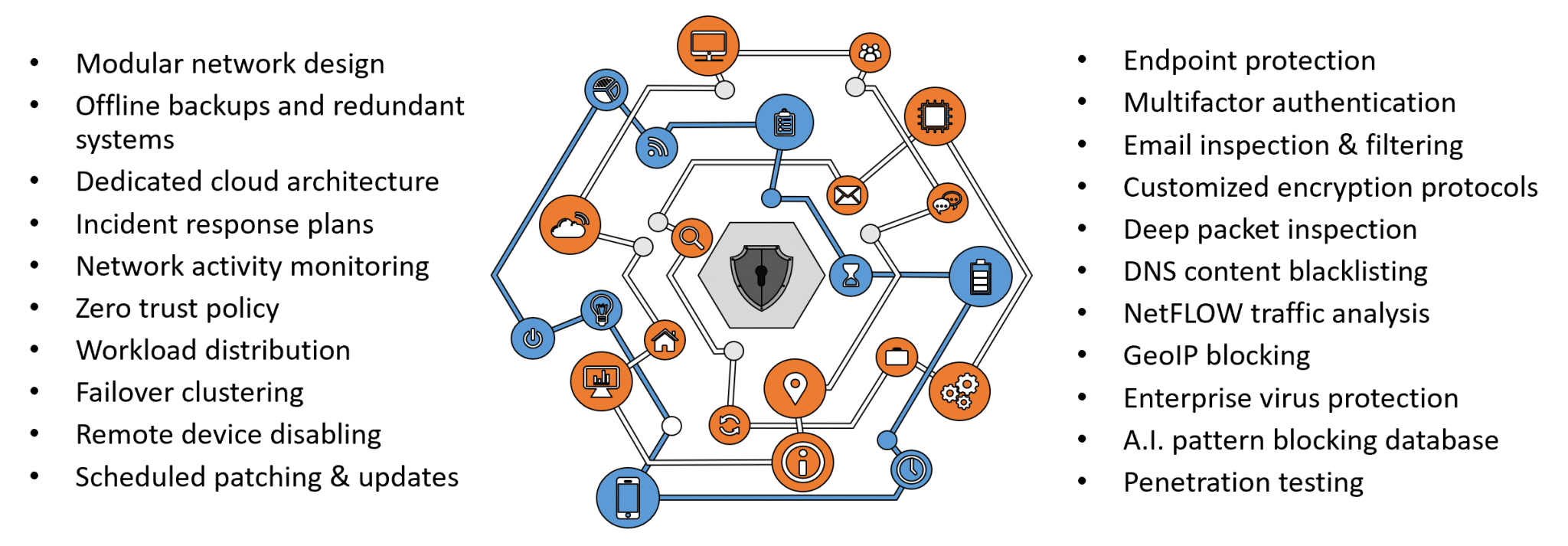
As part of our Zero Trust Security model, we eliminate connections, modulate systems, and only grant access to employees who need access. All access is logged and audited on a regular for irregular activities. All devices have antivirus and antispyware software installed. 2FA is required for all Protected Harbor Clients. And a best-in-breed firewall is installed to block unauthorized access, while remote access should be secured using a virtualized desktop.

We prioritize layered cybersecurity protection, beginning with a sturdy network perimeter composed of a firewall, network management, and regular network inspections. We then include proactive monitoring of your systems, including anti-virus and anti-malware software, DNS filtering, and anti-spam protection. Most importantly, we recommend investing in cyber training for your staff — your employees are the first and finest line of cyber defense.
Cybersecurity Protection Services for New York, New Jersey, & Connecticut Businesses
One IT Company To Keep Your Business, Data, and Customers Secure.
Get a Free Cybersecurity Audit
Understand your security threat exposure with a free cybersecurity risk assessment. Great actionable steps you can take to gain a strategic upper hand. We offer risk assessment services specifically designed for companies operating under HIPAA, PCI DSS, Sarbanes Oxley, or DFARs regulations.
Protected Harbor’s Security Operations Center enables scalable and adaptable threat intelligence and predictive security intelligence for your organization. Our team is staffed with certified security techs and threat hunters from around the globe, operating 24/7/365 as an optional part of your cybersecurity defenses. We are continuously monitoring, detecting, and remediating threats to keep your data protected as part of our elite service plans. When you join The Protected, you..
- Seal network gaps to stop hackers from breaking into your business.
- Maintain high productivity levels by shielding PCs from viruses.
- Avoid costly regulatory fines by complying with data security laws.
- Prevent embarrassing & costly lawsuits by keeping client data safe.
Protected Harbor is continuously collecting flow data to aggregate, analyse, and visualize network details for viewing in real-time or for historical archiving. Our dashboard gives our proactive monitoring team a view of possible threats contacting or attempting to contact the network, including public threats based on IP reputation, high-risk internal clients based on flow count, visual hot spots of inbound connections, top block ports, and recently blocked traffic.
Who’s doing the most traffic? Are we being flooded? What types of traffic are using the most bandwidth? These questions and more are answered by filtering for results on the Top Talkers Dashboard. We can drill down even further on flow details to find specific traffic streams to analyse from an individual protocol or address.



